Vulnerability report system
Today we announce the vulnerability report system, which will allow users to report and keep track of security vulnerabilies on Hex packages.
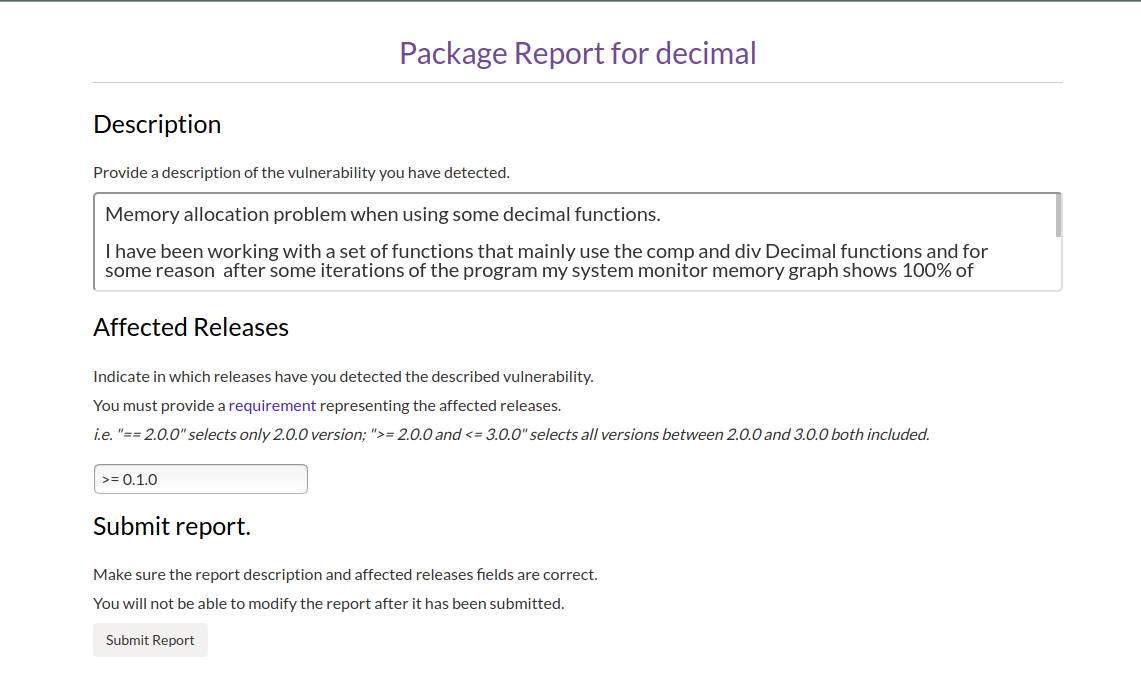
Users will be able to submit package reports through a form accessible from the package page. A detailed description of the vulnerability should be provided as well as any information that might help maintainers to identify and resolve the vulnerability. An affected releases field has also been provided, so the users can specify the range of releases affected by the vulnerability.
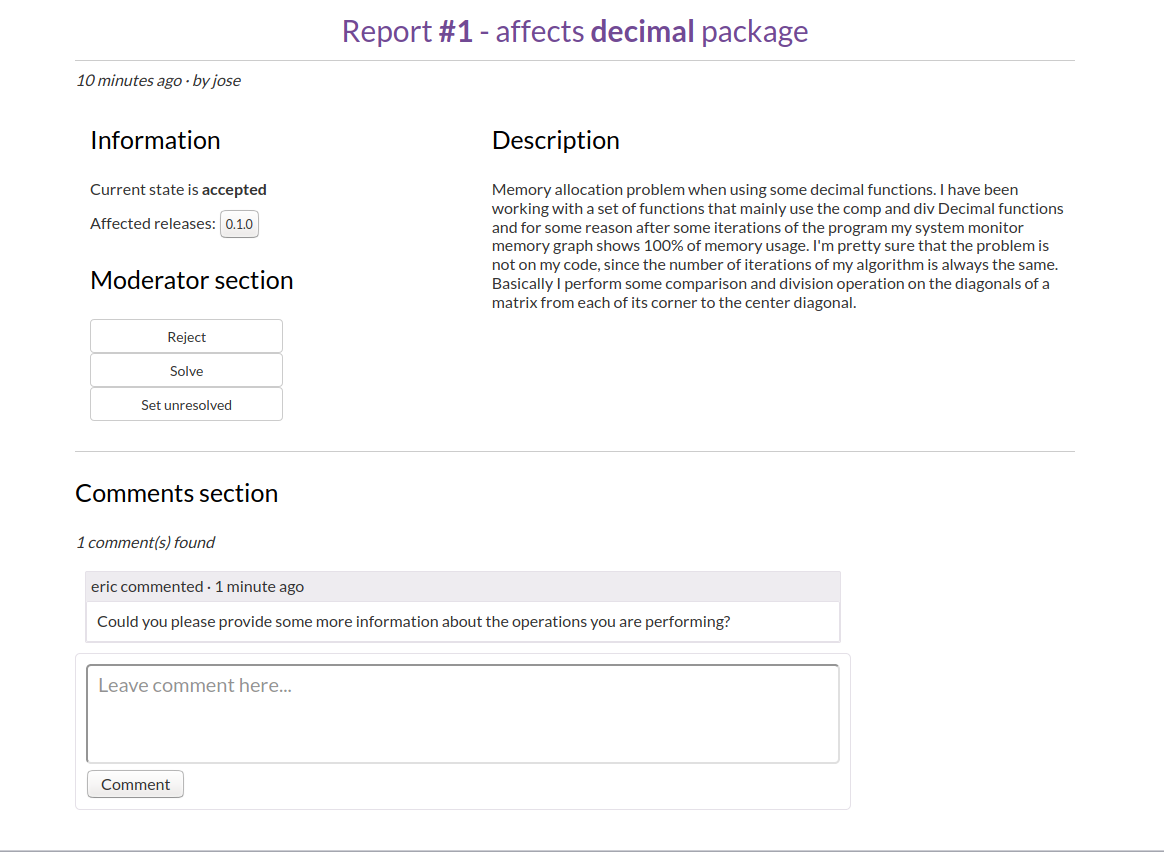
After the report has been submitted it will be published internally and a review process will begin. A group of moderators will review and either accept or reject the report, after a report is accepted package owners will be notified about the report. After fixes for the vulnerability have been released the report will be made public and affected package versions will be marked with the vulnerability. During the process between the initial report and public disclosure moderators will work with the reporter and maintainers to ensure the issue is resolved quickly and correctly.
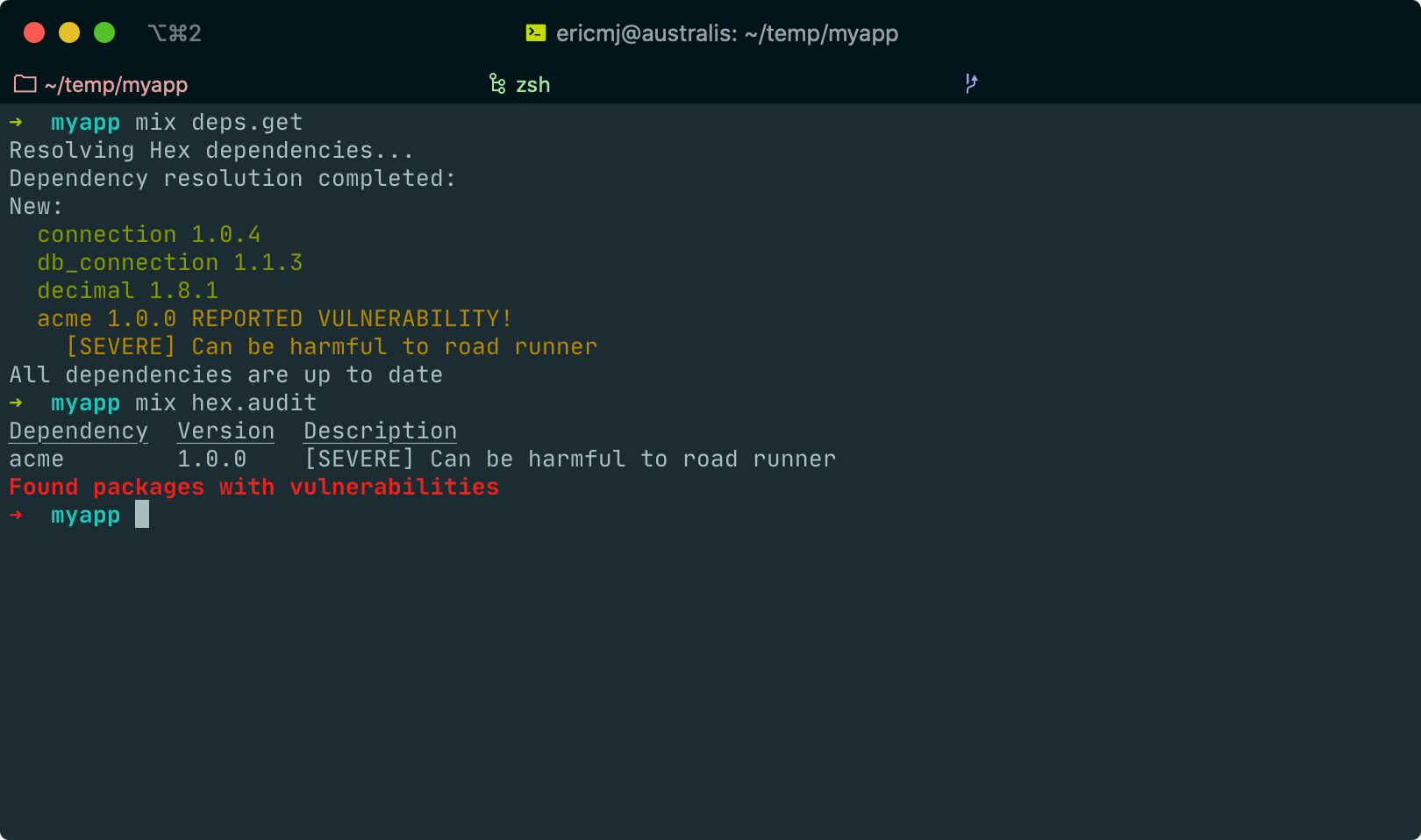
The reporting systems builds upon package retirements to inform users of vulnerable packages when running mix deps.get and mix hex.audit so you can check for vulnerabilities during Continuous Integration.
We will also be providing an API so that external tooling and infrastructure such as Dependabot can use our database of vulnerabilities. Additionally, we plan to integrate with other vulnerability databases such as CVE so that users can be informed of vulnerabilities in Hex packages they use regardless of where they are reported.
The initial group of moderators will be the Hex core team but we hope to be able to include security professionals with experience of information security and vulnerabilities on the BEAM ecosystem so that we can correctly identify valid security reports and give support to maintainers to fix the issues.
The vulnerability report system has been merged into hex, but is currently hidden behind a feature flag while we test it internally and work out the final kinks.
Many thanks to Lois Soto Lopez who developed this feature as part of Google Summer of Code 2020.